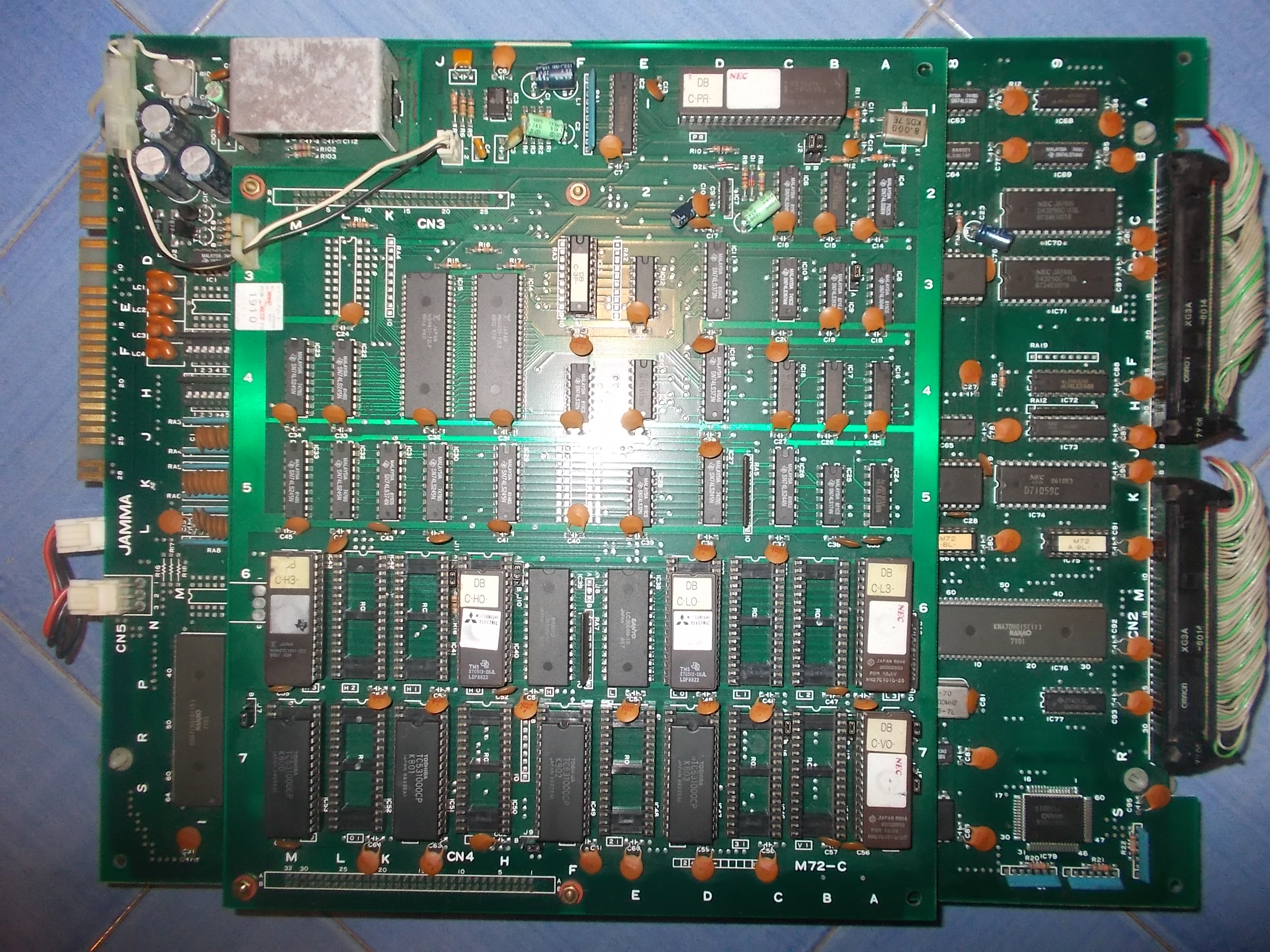
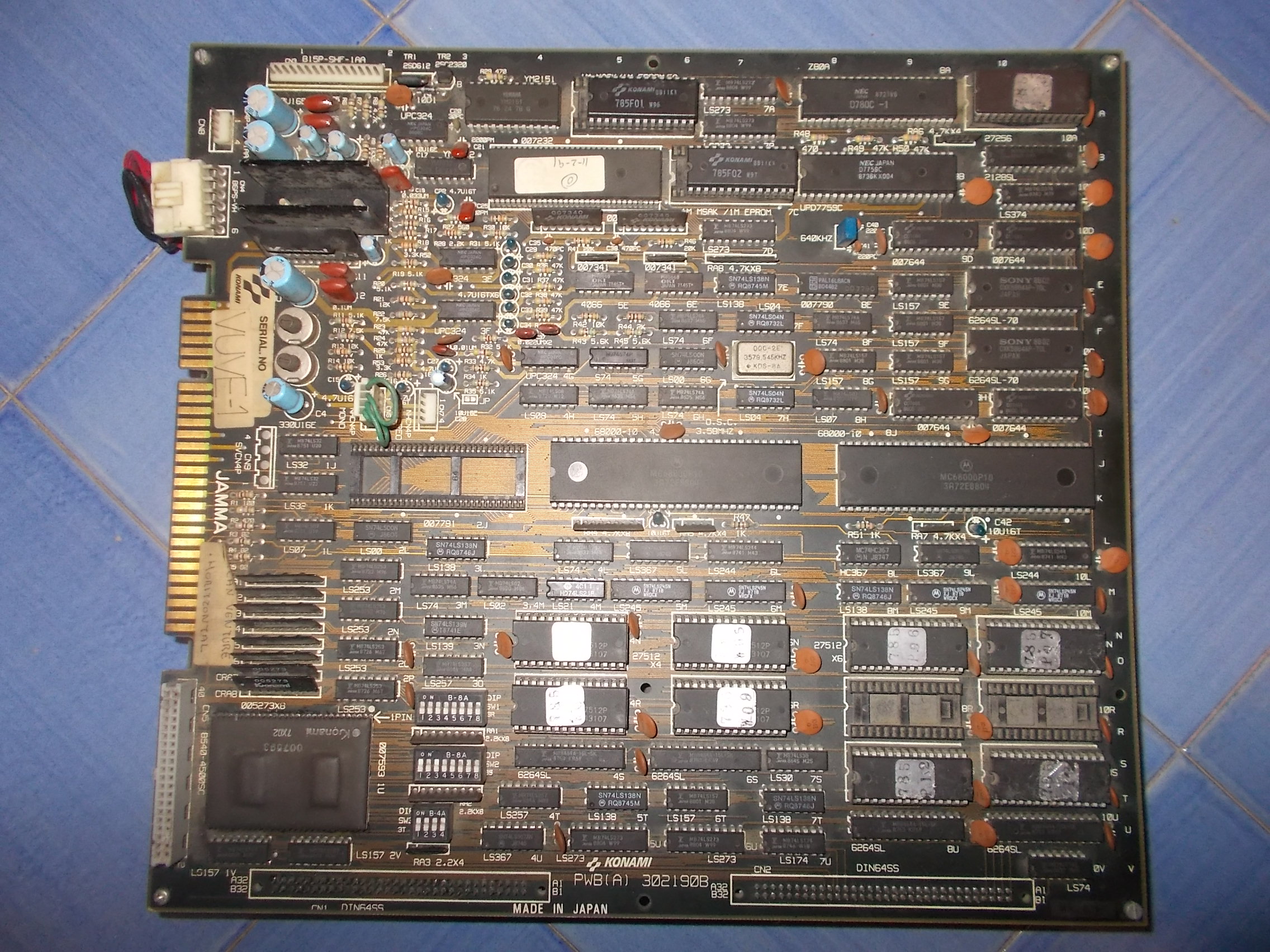
Received from Spain this faulty Vulcan Venture PCB (export release of Gradius II on the glorious’ Konami Twin16 hardware)
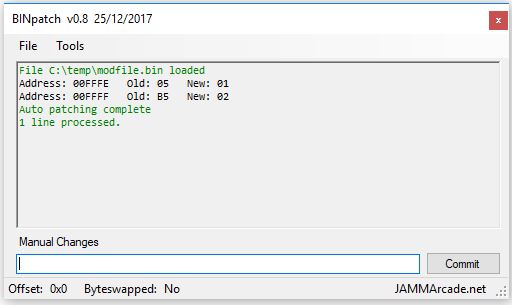
This is what I got once powered it up:
Graphics were all corrupted, you could barely recognize the self-test procedure which failed all the time causing the reset of the whole system in an endless loop.I focused my troubleshooting on VIDEO board:
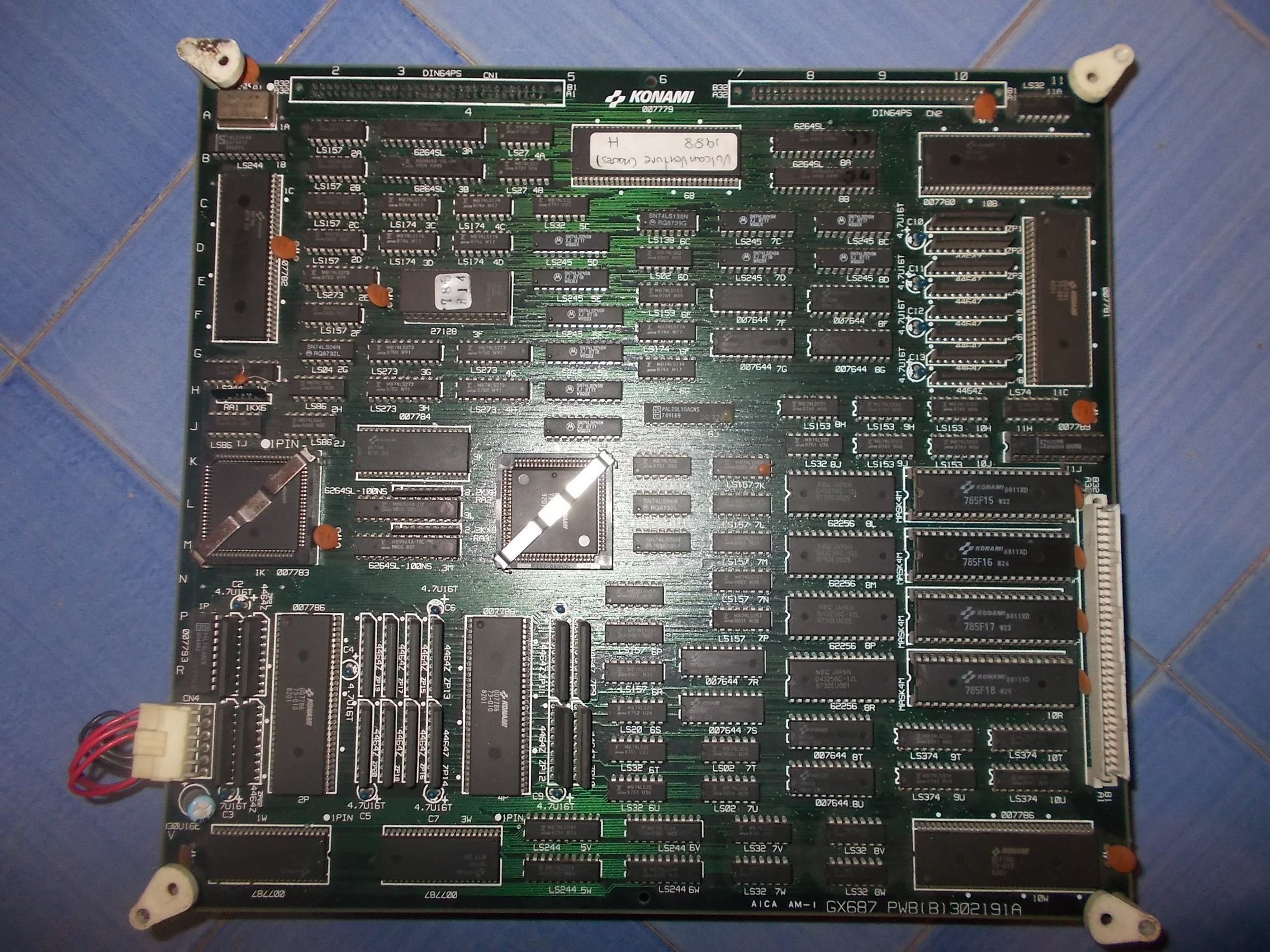
Like the CPU board, also the VIDEO one was almost fully populated with Fujitsu TTLs but before going thru them I started to probe the various RAMs.I found one 62256 @8L with dead outputs:
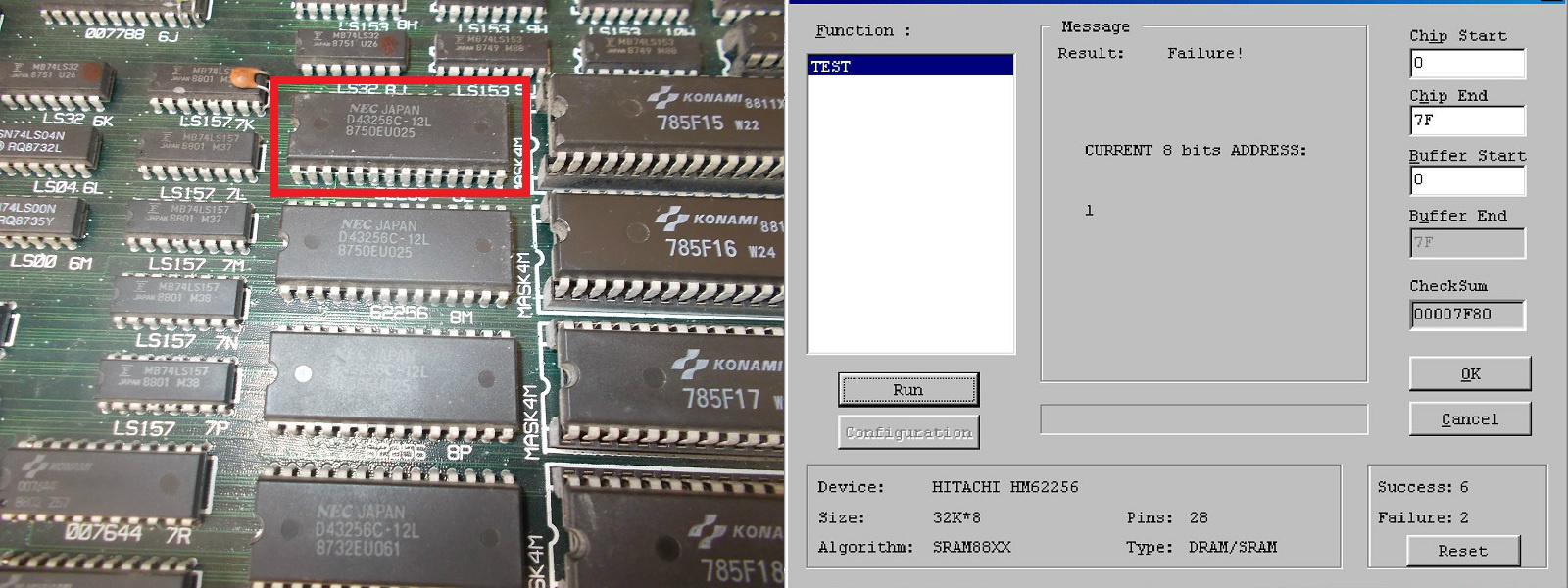
This finding lead to no improvement.So I fired up my logic comparators and started to probe TTLs.Sequentially I was able to locate these faulty ones, all of them on VIDEO board and from Fuitsu:
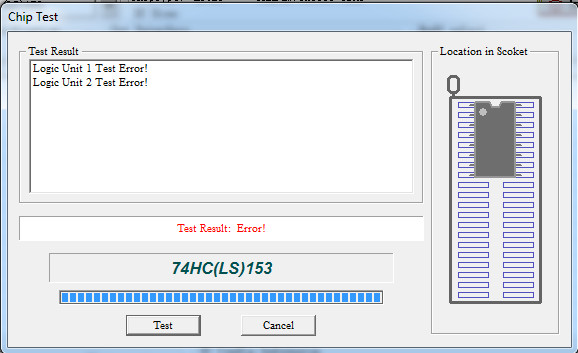
- 74LS153 @9H
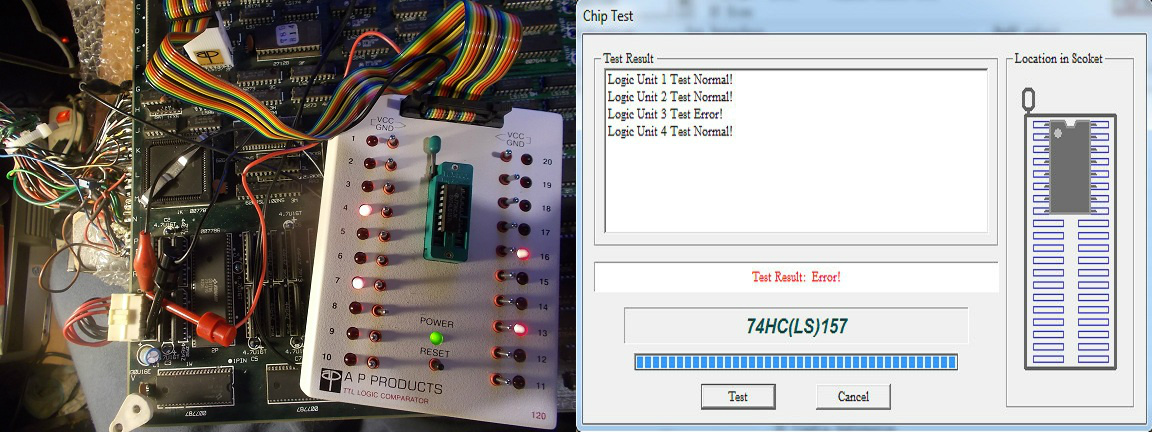
- 74LS157 @2F
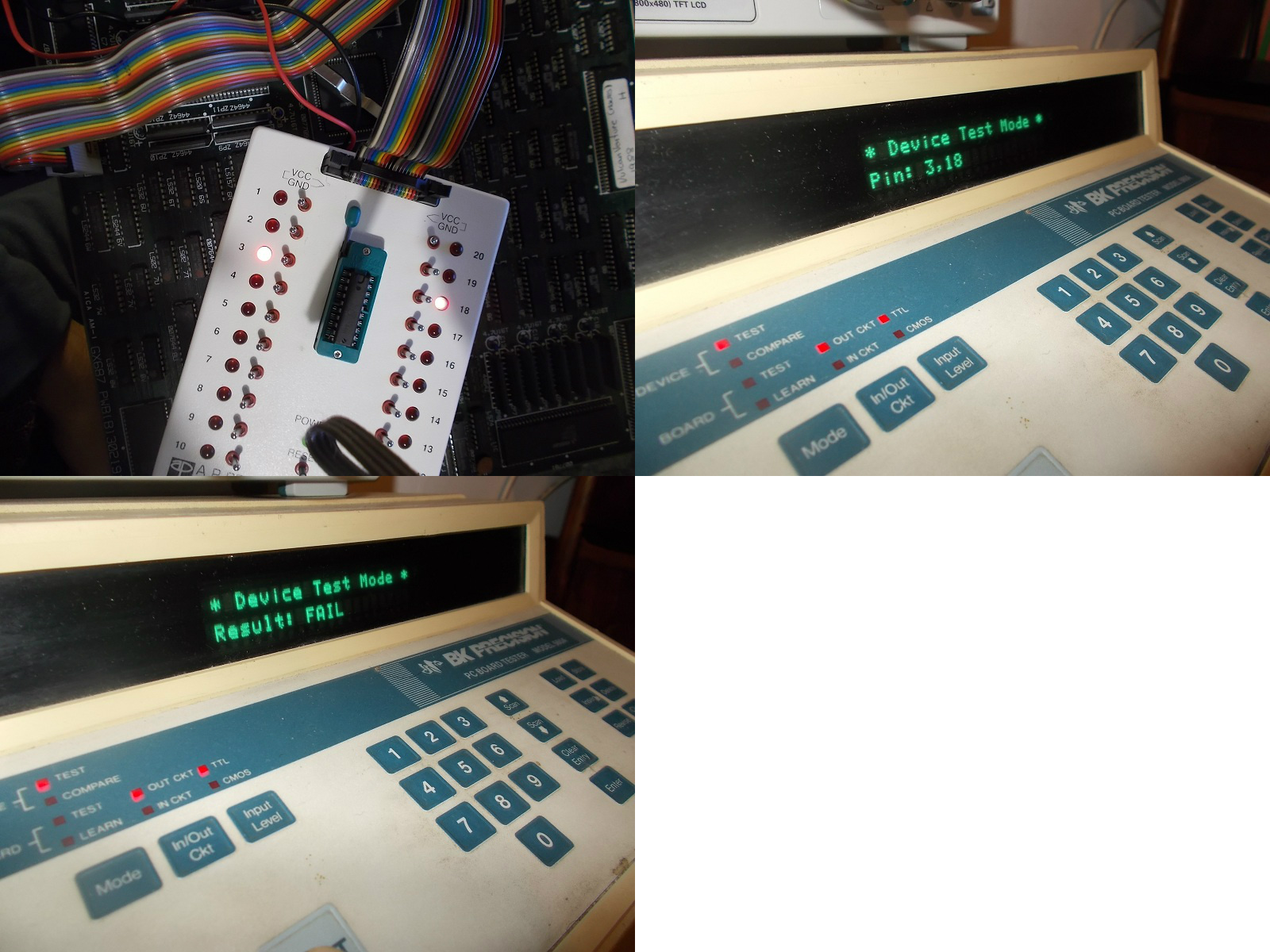
- 74LS244 @5W
But the board was still not booting :

Shorting some data/address lines of two 6264 SRAMs @3A and 3B changed the garbage on screen so this was the path to follow, the problem was in the tilemap generation circuit which these RAMs are part of :

Probing the RAMs revealed that the R/W lines (pin 27) of both were stuck high, according to schematics these signals come from a 74LS27 @4B:
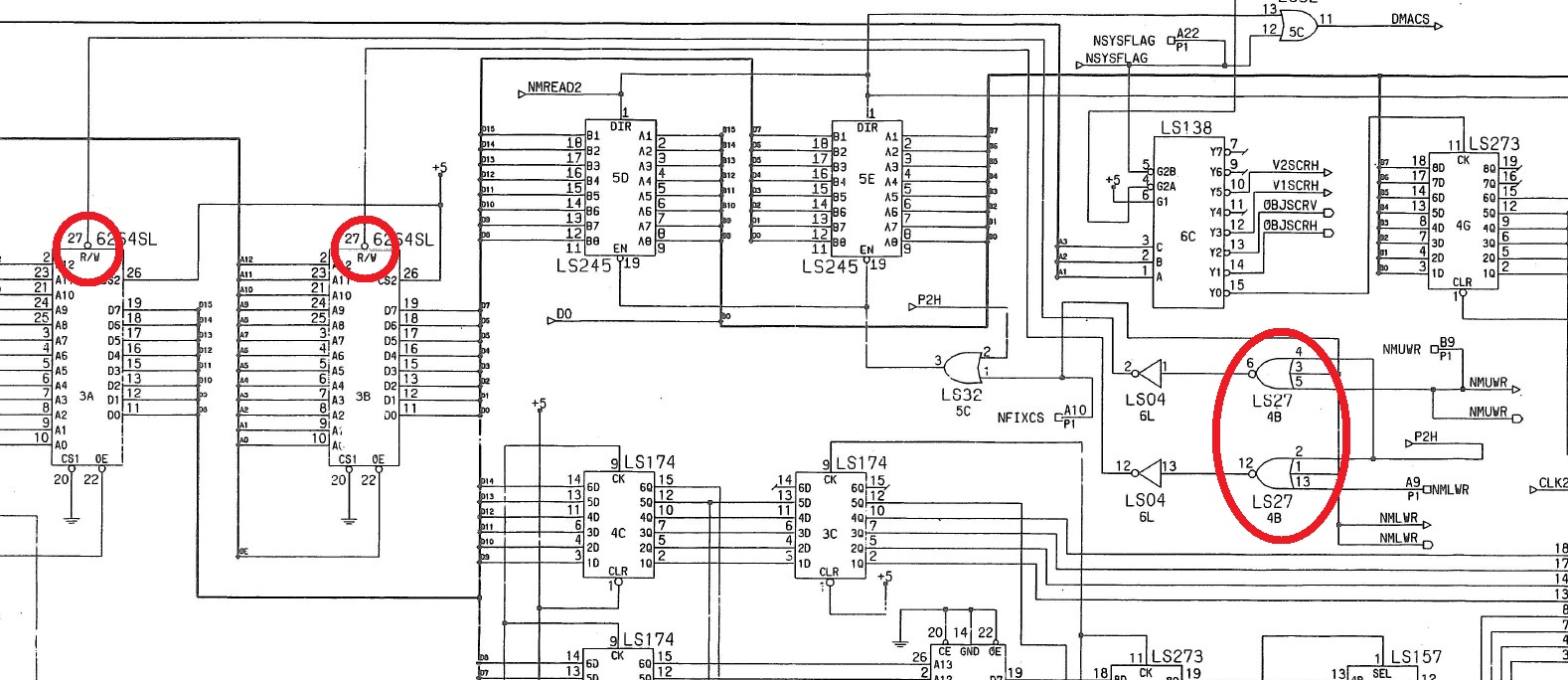
My HP10529A logic comparator confirmed troubles on two outputs of this 74LS27 which failed when tested out-of-circuit:
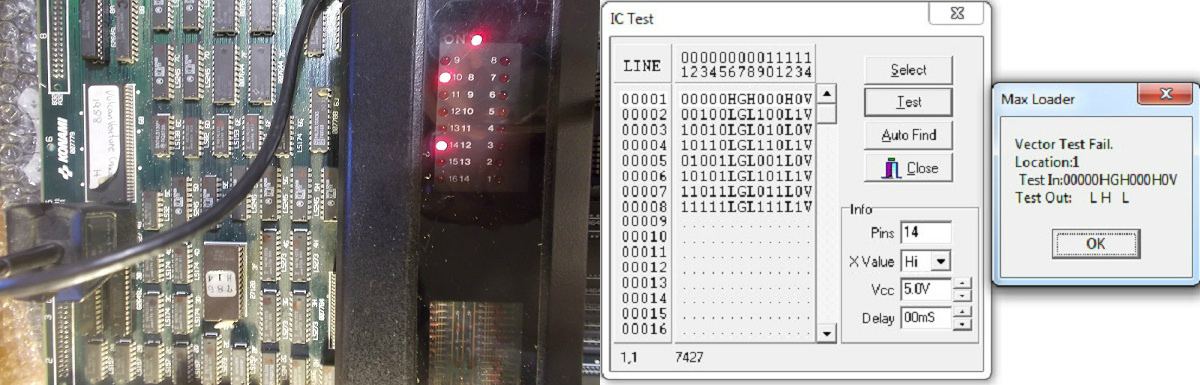
Now board succesfully passed the self-test and entered in game fully playable with sound but all graphics had very noticeale jailbars:
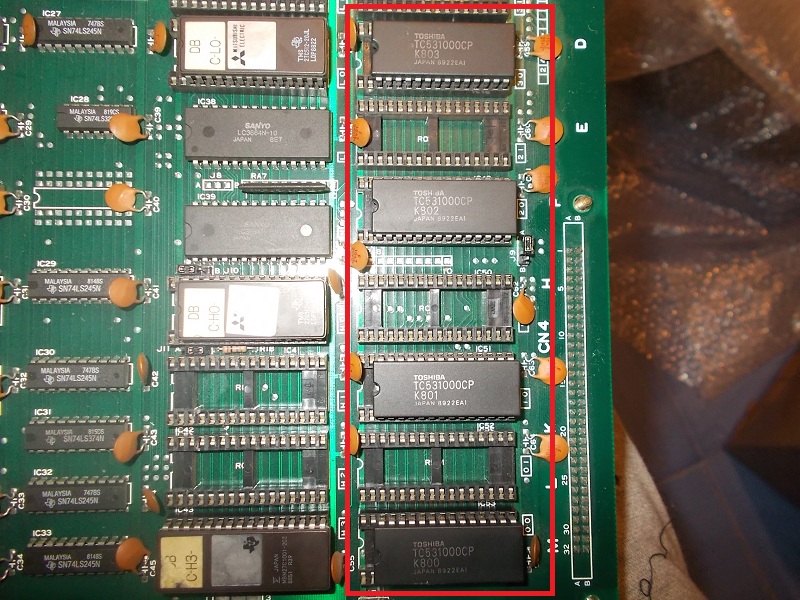
Most of graphics data is stored in four 4Mbit MASK ROMs:

While dumping them my programmer reported troubles for the ones @10L and 10M:
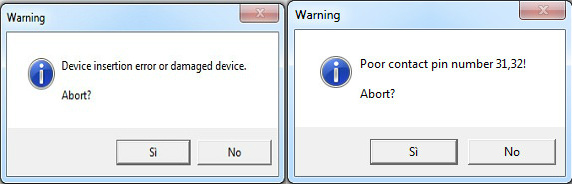
Replaced them with two 27C400 EPROMs fixed the issue and board completely.

Evil Konami (and Fujitsu) defeated again but war is not over.See you to next battle…